Operational Capabilities
From high-level logic to transistor-level analysis.
Offensive Security & 0day R&D
Development of custom offensive tooling and working exploits for authorized agencies. Research into zero-day vulnerabilities across modern software stacks. Penetration testing and source code review (C/C++/.NET, PHP, Java, JavaScript/TypeScript, Python, …) delivered with researcher-grade depth.
- Exploit Development
- Source Code Audit
- Network Assessment
- Red Teaming
Embedded & Hardware
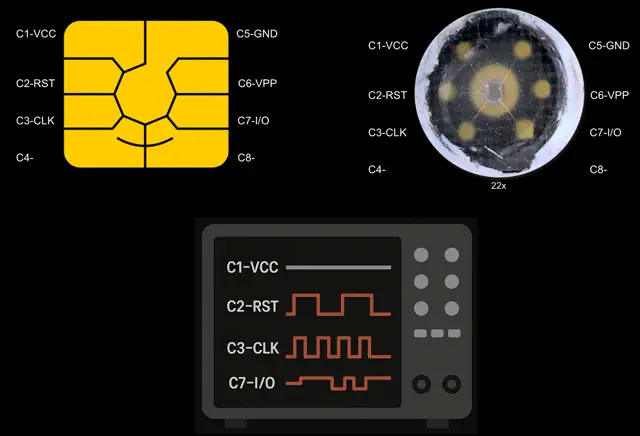
Security testing for IoT, routers, and appliances. Low-level analysis including chip-off memory dumping, glitching (CPU/Power) to bypass hardware protections, firmware extraction, and side-channel evaluations (SPA/DPA).
- Firmware Extraction
- Chip-off Dumping
- Glitching
- Side-Channel (SPA/DPA)
Radio Frequency (RF)
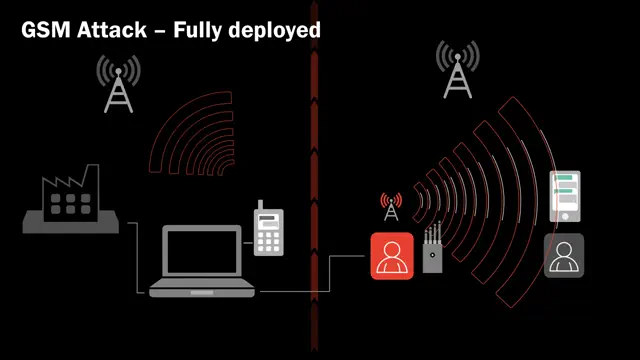
Analysis of unknown over-the-air protocols and crypto cracking. Resilience testing against jamming attacks. Reverse engineering RF stacks to surface logic flaws and exploitable bugs.
- Protocol RE
- Signal Analysis
- Jamming Resilience
- Crypto Attacks
Defensive Engineering & Forensics
Post-disaster recovery and forensic analysis to trace attack vectors, remove backdoors, and recover from ransomware events. Secure network architecture design, WAF configuration, and firewall planning for maximum resilience.
- Incident Response
- Ransomware Recovery
- Forensics
- Architecture Design